Research & Development
Annual Report 2018
UNIVERSITI TUNKU ABDUL RAHMAN

Centre for Information Systems and Software Technologies
(CISST)
ACTIVITIES REPORT
| No. | Event & Date |
|---|---|
| 1 |
IoT for Agriculture: From Farms to Future Cities With the plan to find effective solution to grow and distribute organic food within the cities, the research project focuses on having crops grown in well-controlled indoors environments, and using sensor, wireless and cloud technology to distribute the crops. Dr Goh mentioned that the idea was to improve the urban lives through the data gathered from information technology. One of the aspirations of the research team is to implement the research project in major cities of Malaysia, such as Kuala Lumpur, Johor Bahru, and Penang. “We can use idle spaces within cities such as Kuala Lumpur, Penang and Johor Bahru to grow food, this will reduce delivery cost and carbon footprint to transport food from outside the city. And by using cloud and analytic technology, we can build an intelligent transportation system to find the best routes to distribute the fresh produce”, explained Dr Goh.
|
| 2 | An Overview Of Aspect Based Sentiment Analysis In Twitter Twitter has become a popular social media service, where 500 million tweets are sent per day and 200 billion tweets per year. The text of the status update, typically limited up to 140 characters. From Year 2017 onwards, twitter no longer limits reply tweets to 140 characters. When comparing to blogs, the shortness of tweet facilitates the user to convey messages faster and easier in seconds. Sentiment identification in Tweets garnered the researchers’ interest in language processing as well as in political, social sciences, and customer product reviews. The task usually involves detecting whether a piece of text expresses a POSITIVE, a NEGATIVE, or a NEUTRAL sentiment, and the sentiment can be general or about a specific topic, such as a product, a person, or an event. Dr. Ramesh briefly discussed on Aspect based Sentiment Analysis in twitter and then walked through opinion mining and sentiment polarity.
|
| 3 | Mathematical Tools for The Analysis of Collision Attacks
Advanced cryptanalytic search algorithms like van Oorschot/Wiener's parallel Pollard-rho collision search and time-memory trade-off methods (e.g., rainbow tables) use so called "distinguished points" to find collisions or preimages of a function 𝒇:𝑿 𝑿. The set 𝑿 is the search space, 𝒇 is typically a one-way function that is mathematically modelled as a random function and the distinguished points are the members of a small subset 𝑳 of 𝑿. The aforementioned cryptanalytic algorithms pick start values and iterate the function 𝒇 until a distinguished point is reached and repeat this parallelizable procedure over and over again. With the results of this search the particular cryptanalytic task can be achieved. A thorough analysis of success probabilities and run times of these algorithms is very difficult, most results in this direction are based on heuristics. In this talk, Professor Georg Illies introduced some tools, in particular, generating functions of several variables that deliver answers to some of the emerging questions. The topic is a mixture of combinatorics, analysis, probability theory and cryptography. |
| 4 | An Overview Of Side-Channel Attacks Against Ecc And Countermeasures Speaker: Professor Georg Illies Date: 1 March, 2018 Time: 10:30 am - 11:30 am Event Type: Talk Venue: N109, Block N, FICT, UTAR (Kampar Campus) Participants: 16 
Public key schemes based on elliptic curve cryptography (ECC) have become increasingly popular as their bit security level increases linearly with the key length in contrast to "classical" rivals like RSA, DH and so on. There are a lot of cryptographic devices, in particular, chip cards in real use that rely on ECC implementations. Nonetheless, ECC has been found vulnerable to side-channel attacks in a similar manner as RSA and the like. |
| 5 | How mighty the deep learning machines are! Why are people still looking for a new DL architecture? Speaker: Prof.Zen Chen Date: 30 March, 2018 Time: 10:00 am - 11:00 am Event Type: Forum Venue: NF023, Block N, FICT, UTAR (Kampar Campus) Participants: 13 
These days we often hear that a computer program, AlphaGo, using Deep Learning defeated the Go world champion in 2016 and in China an AI robot called XiaoYi passed the medical licensing exam in 2017. All these news stir up the worry of human about losing edge to the AI machines. However, if the machine is really mighty, why are people/companies still looking for a new DL architecture? Right now, DL is still like a black box or a mist, hard to understand. Undoubtedly Artificial Intelligence is making profound effects, but will it become dead again as before? On the other hand, is it true that only human can develop into a mighty expert, but not the machine? If so, what kind of human expert knowledge can be transferred to the machine? Currently, for the tasks of image (and speech) classification, localization, detection, segmentation, understanding, etc. how can the machine learn from the human experts?
|
| 6 | The Art of System Monitoring Before 2013, Dr. Alex thought that the concept of monitoring is rather simple and straightforward. It is basically just a distributed system that is designed to observe and check the changes of a process or a system's state over a period of time, and to generate alerts when there are events. He realized that he overlooked the challenges of developing an effective monitoring system when He started a project on crowd tracking with a company for retail businesses. He learned the challenges of system monitoring in a hard way. In this talk, he share his experience with all of us. |
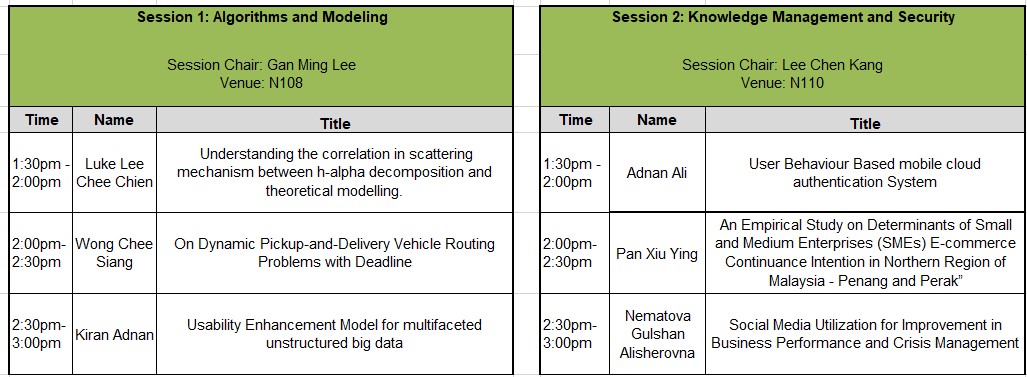
| 7 | The FICT Postgraduate Colloquium (May 2018) CISST and FICT have organized first FICT Colloquium of the year on 15th May, 2018. In this colloquium, all postgraduate students (both Master and PhD students) presented their recent work or findings in their field of research.
|
| 8 | Importance of Personality in Software Engineering In this talk, Dr. Mobashar shared the importance of human factors in software engineering. Previously, the research studies which were done in software engineering field mainly focused on the technical aspects and ignored human factors. However, now the number of research papers stating the importance of non-technical factors (human factors) in this field is increasing. Research on these factors may not solve all the problems in software engineering, but it will give insights and new approaches to improve the quality of software, increase the productivity and motivation of software engineers. |
| 9 | Bootstrapping Malay Dialect Models on Text and Phonetic Analyses in Text-Tospeech System Text-to-speech (TTS) technologies have matured and they have been equipped and embedded in many tools, for instance in mobile phones, robotics and telephony system. For building a TTS system, resources that required are speech corpus, pronunciation dictionary and text. Nevertheless, building an under-resourced Malay dialect TTS system is challenging. The problems of limited language resources in Malay dialects include inexistence of Malay dialects pronunciation dictionaries, quasiunknown of the sets of Malay dialects phonemes, no standard orthography in Malay dialects and limited written text of Malay dialects. TTS system involves text analysis, phonetic analysis, prosodic analysis and speech synthesis. In this talk, Dr. Jasmina shared her study on text analysis and phonetic analysis of under-resourced Malay dialect where a framework of under-resourced Malay dialect TTS system has been proposed. |
| 10 | Research Talk and Meeting with Dr. Dimitrios Piromalis It is a research talk and meeting with Dr. Dimitrios Piromalis. He has shared with us the topic of “Open-source Hardware Arch. for Wireless Sensors Nodes”. |
| 11 | Research Talk and Meeting with Prof. Theodore Ganetsos It is a research talk and meeting with Prof. Theodore Ganetsos. The session is divided into three parts as following: |
| 13 | Research Talk and Meeting with Assistant Professor Michal Papoutsidaki It is a research talk and meeting with Assistant Professor Michal Papoutsidaki. The session is divided into two parts as following: |
| 14 | E-Commerce Continuance Intention Among Small Medium Enterprises (Smes) in Malaysia The main aim of this study is to investigate the factors influencing the continuance intention of e-Commerce among small-and-medium enterprises (SMEs) in West Malaysia. There have been many success stories of e-Commerce worldwide. Among the famous ones are the Amazon.com and Rackspace. Nonetheless, according to the survey conducted by the Associated Chinese Chambers of Commerce & Industry of Malaysia (ACCCIM), e-Commerce adoption rate among SMEs in Malaysia is relatively low, i.e. 28% out of 965 e-Commerce activities involved (ACCCIM, 2012) and 24% of the respondents claimed that they are planning to use e-Commerce. In the proposed model, there are five independent variables name, perceived benefits, perceived barriers, top management, organization readiness and external pressures used to access the relationship between the e-Commerce continuance intentional among the SMEs. The statistics are indeed discouraging while noting that e-Commerce is one of the main factors for strengthening the competitive advantage of SMEs when compared to their larger counterparts. A comprehensive data collection approach will be applied in this research, follow by rigorous data analysis using various statistical and soft computing methods. Dr. Lim stated that they hope to provide managerial insights into the e-Commerce continuance intention among SMEs in Malaysia. Thus, facilitating eCommerce owners or even policy makers in gaining valuable information and understanding of eCommerce trends, applications and retention strategies.
|
| 15 | NetSim There was a short technical sharing session given by Bymetrix. The sharing session in UTAR is about NetSim. NetSim (Network Simulation & Emulation Software) that used by over 300 educational institutions globally for network lab experimentation & research.
|
| 16 | COMPUTER AIDED 3D SKULL – 2D FACE SUPERIMPOSITION IN FORENSIC ANTHROPOLOGY Identification of humans via Craniofacial Superimposition (CS) is one of the prominent research areas in forensic science. Basically, CS is a forensic imaging technique used to identify an unknown skull by matching it with the available face photographs of missing individuals. Life-size enlargement of the face image and orientating the skull to correspond to the posture seen in the face photograph are the two main problems that exist in the conventional as well as in the computer-aided CS.
|
| 17 | Child Tracking System in Shopping Mall with AR Interface Shopping malls are public spaces used by individuals for various reasons. Thousands visitors come to a shopping malls every day. Here, all components of the social and physical environment interact and have an impact on social participation. Not only do visitors quickly lose track of what is going on there and quickly miss good and it is particularly problematic for parents whose children can no longer be found or the car cannot be located in the large car park, even after a long search. The worse when children regularly get separated from their parents at shopping malls. Case of lost children in a shopping mall can be said to occur almost every day, indicate that at least five cases of lost children were reported every month in the shopping mall. As the cases of lost children in shopping mall getting worse, this work proposes a Location Tracking System (LTS) to track child in indoor shopping mall. LTS was developed via received signal strength indicator (RSSI) to measure the location of the child and keep track the child movement seamlessly. In addition, to get easy for the parents to monitor the child movement and location, the Augmented Reality (AR) application will be integrate. In this talk, Dr. Nur Haliza stated that the proposed work will be gorgeous for parents not only reduce of their afraid loosing child but the interface of this application was interesting and user friendly to parents to exactly monitor their children.
|
| 18 | Game Theory in Everyday Life Why the first batch of inventor-cum-entrepreneur always failed? Why traffic jam and queue cutting issues have never been solved? Should women be wearing make up? If you are unable to see the link between these questions to game theory, do not worry, you soon will. Game theory is everywhere, and you do not have to be a computer geek to understand its most insightful aspects. In this talk, Dr. Cheng explained the notion of a Nash Equilibrium and illustrate its applications on realworld examples.
|
| 19 | Tactics under the Current Industrial Trend Dr. Choo introduced the portal fict.southeastasia.cloudapp.azure.com, the current industrial trend, and some typical companies. He also motivated some tactics for establishing engagement with companies, such as visitation. We will then be more facilitated to eye on the possibility of research collaborations.
|
| 20 | H2020 EU-TW 5G-Coral: Research Roadmap and
Results on Mobile Edge Computing 5G-Coral is an H2020 EU-TW project with Taiwanese and European partners, including NCTU, ITRI, ADLink, UC3M, Ericsson, InterDigital, Telecom Italia, SICS, Telcaria, and Azcom. The path toward 5G presents a clear trend of carrying out computations close to end users. By further utilizing pervasive computational resources in proximity to users, edge and fog can be merged to construct a distributed computing platform, which could also serve as a common stage for multiple radio access technologies (RATs) to increase communication capacity, and hence opens a new dimension of multi-RAT integration. In this talk, Prof. Lin first introduced the concept behind the vision of facilitating multi-access convergence via edge/fog computing, along with open problems and challenges that should be addressed to turn such a concept into reality. Then, an overview of the research roadmap on 5 key components utilizing communications and computing resources was given, including service chain routing, multi-RAT offloading, multi-tenant slicing, horizontal and vertical federation, and capacity optimization. Selected results are then presented. Key findings include (1) the 3-tier architecture with edge computing saves about 20.7% capacity cost over the traditional 2-tier architecture, with 70% of capacity allocated to the edges; (2) multi-RAT offloading reduces about 40% capacity cost with a large number of UEs; (3) some use cases in 5G would capture 1.5 to 2.3 times more resource than required, if without slicing; (4) the low-latency authentication with MEC reduces over 90% overhead if done with the cloud.
|
| 21 | Turing Machine Turing Machine is not Dr. Savio research area, but it can give us tough training in Theoretical Computer Science. Turing Machine was invented by Alan Turing in 1936. His status in Computer Science is the same as that of Issac Newton in Physics. When he published his idea, no one understood him except Ada …
|
| 21 | Smart factories: Examples from South Korea and Sweden (Paper Sharing) Manufacturing is undergoing major changes in term of digitalization, technology development and environmental concern, driving a renewal of industrialised countries such as Sweden and South Korea. In this talk, Dr. Chang mentioned that this paper use examples from South Korean and Swedish SMEs and large companies, in an effort to bring the high level smart manufacturing concept to the concrete. The examples contribute to the definition of smart factory and its corresponding development scheme by discussing key enabling and hindering dimensions for building the "smart-factory-capability" of a company.
Reference: Wiktorsson, M., Do Noh, S., Bellgran, M. and Hanson, L., 2018. Smart Factories: South Korean and Swedish examples on manufacturing settings. Procedia Manufacturing, 25, pp.471-478.
|
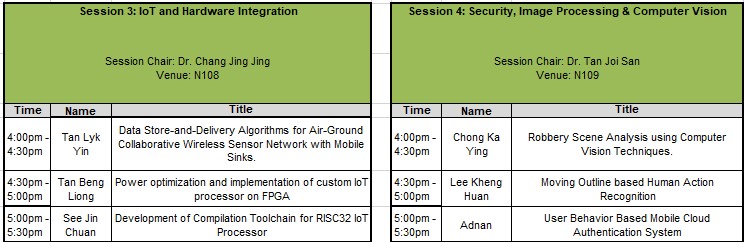
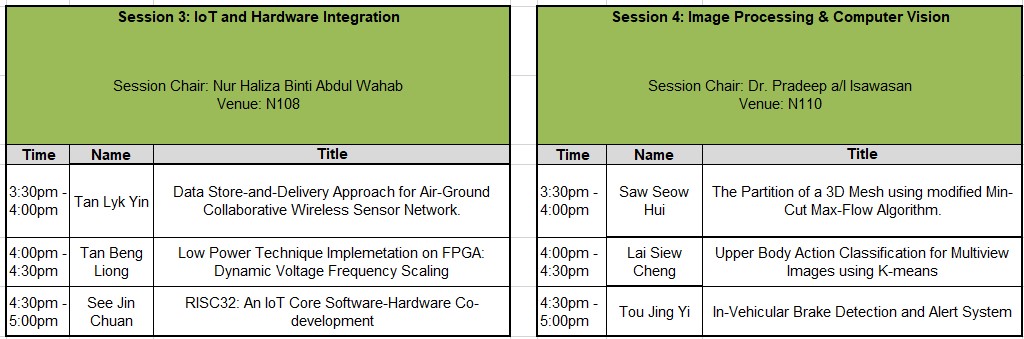
| 22 | The FICT Postgraduate Colloquium (December 2018) CISST and FICT has successfully organized the second FICT Colloquium of the year on 13th December 2018.
In this colloquium, a total of 12 FICT postgraduate students have presented their works and about 40 participants have attended the event. The session chairs were Dr. Gan Ming Lee, Dr. Lee Chen Khang, Dr. Nur Haliza Binti Abdul Wahab and Dr. Pradeep a/l Isawasan. The presentation duration for each student was 30 minutes. The presentation of each student was evaluated by the session chair and a feedback form was returned to the presenter for future improvement.
|
23 | Developments of 3D Virtual Visualization and 3D Printing Models Based on MR Images for Supporting Uterine Removal Surgery Uterine surgery is a common operation that routinely performed for the treatments of the uterine lesions such as fibrosis and cancers. Pre-surgery-planning is necessary and needs patient information that can only interpret from magnetic resonance images (MRI). The raw data of MR images involves huge unstructured information about patient specific anatomy with lesion’s situations, which cannot be institutively and quickly extracted by using conventional MRI interpretations (observing a number of twodimensional (2D) sections on a screen). A computer system that extracts and processes that useful information from such a raw image data according to varied purposes, and provide a institutive userinterface for surgeons is strongly expected. This work proposes a novel approach to demonstrate the interesting information in MR images to surgeons institutively by generating 3D patient specific models with transparent and elastic materials. Dr. Sayed mentioned that their aim is to address three critical issues during the pre-surgery planning; (1) Inefficient of the conventional MR image interpretation methods for surgeons; (2) un-intuitively understanding of 3D anatomical structures on computer displays. (3) Ambiguous sense of the 3D distances and sizes between lesions and related tissue regions, which is important in surgical operations.
|